Ersatz Luxury
Copycat hardware has been a significant problem in the manufacturing world. The problem isn’t unique to electronics:
Respondents were most likely to have knowingly made counterfeit purchases of ‘Clothing, Footwear and Accessories’ and ‘Sports’ products, with 13% and 9% (respectively) of consumers of those categories having done so in the past year. Other categories experienced notably lower levels of counterfeit purchases: Beauty & Hygiene (6%), Electricals (5%), Toys (5%) and Alcohol (2%).
There was a singular, given reason:
[T]he main motivation, by some way and consistent across all respondent groups, was
cheaper price . No other single motivation was selected by more than a third.
This issue extends beyond fashion to electronics, handbags, watches, and medications. The total value of counterfeit and pirated goods reached
$3 trillion in 2022 , tripling since 2013.
This has led to frequent public awareness campaigns focusing on the fate of confiscated counterfeits:


Manufacturers spend years developing and perfecting a product, then releasing it to the masses, only to have the intellectual property copied and cheaper models flooding the market.
One of the most notorious examples was the seemingly ubiquitous Hoverboard, introduced in 2013. By 2015, it was a consumer phenomenon:
By the end of 2015, 40,000 boards were coming into the U.S. each day. While nobody tracks total sales, manufacturers have shipped more than $2 billion worth of hoverboards over the past year and a half, by Fortune’s estimates.
By 2018, they were subject to a U.S. Consumer Protection Safety Commission warning letter, ultimately leading to a recall in 2023.

The root cause of all this was counterfeit versions of the original design, built using shoddy parts, software security issues, causing harm to riders, and unsafe batteries that had a tendency to, as NASA folks might say, perform High-Temperature Excursions.
A key problem was that there was no way to determine the authenticity of a real, certified Hoverboard. There were so many knock-offs, at all different price points, that confidence in them quickly eroded.

Blew Up. Grade A headline-writing.

The same problem was faced by other hardware manufacturers, like San Francisco-based Logic Analyzer maker Saleae, or Santa Cruz-based OneWheel
# SourceI am a happy, long-time owner of an authentic Saleae Logic 16, which I used while working on early versions of the OneWheel.
Both companies had issues with counterfeiting.
Saleae Logic
Saleae Logic, a small San Francisco-based company, makes one of the best Hardware Logic Analyzers at a price point accessible to professionals, DIY Makers, and hobbyists. Its killer feature was the software that ran on a desktop computer and could show a variety of data points necessary for debugging device communications.
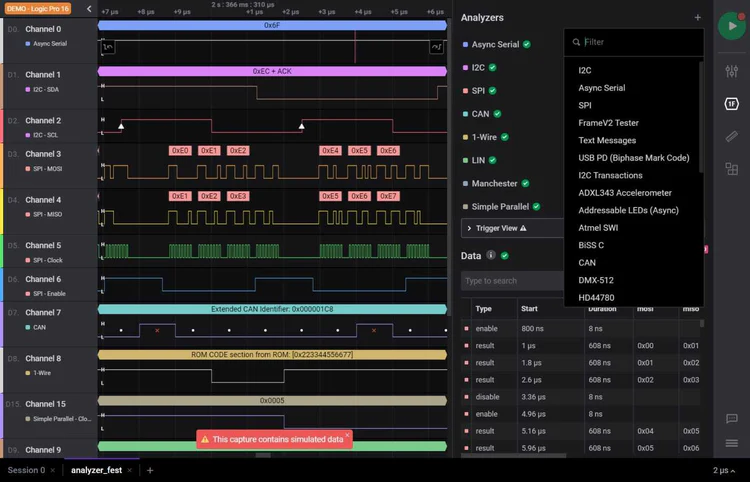
The hardware itself was compact (and beautiful), but it was the software that shone. You would purchase the hardware, plug the device into your computer, then download and install the software – at no additional cost. The app would discover the device and do its magic. The software was frequently updated and was itself extensible via plugins.
The problem was that the software failed to verify the hardware was actually made by Saleae.

This led to a rash of cheap, knock-off devices you could purchase on eBay for a fraction of the price:
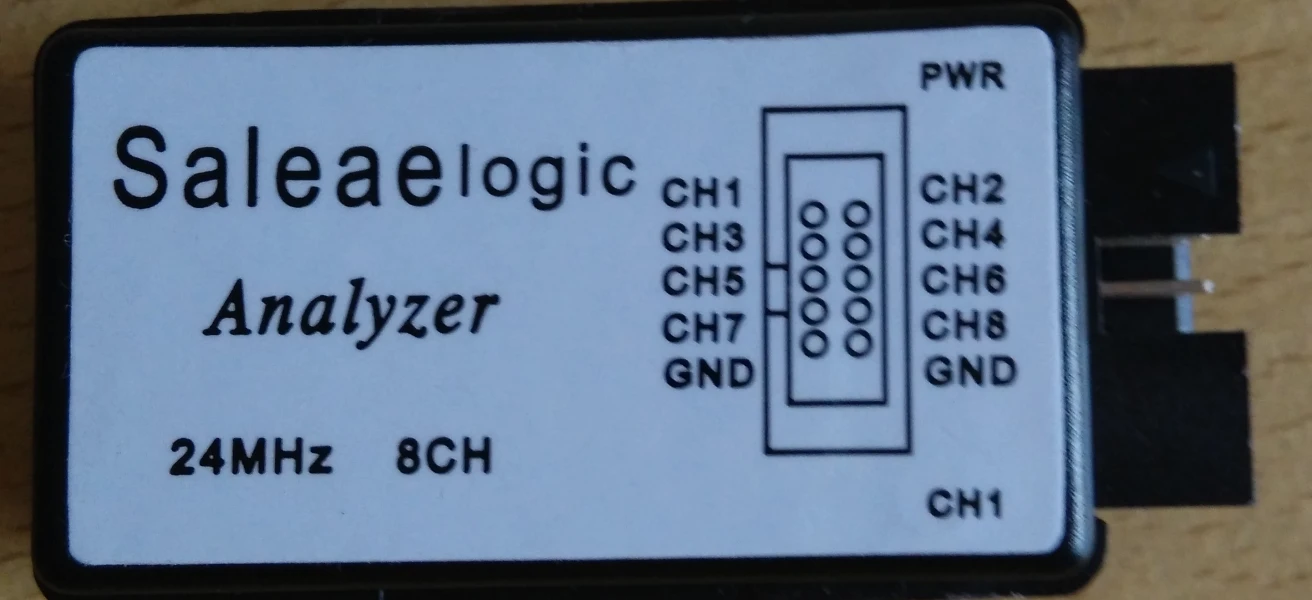
As mentioned previously, since this is a counterfeit of the original Saleae product, the seller does not provide any software tools to use it. Instead, they will redirect you to download the software from the Saleae website, detailed instructions will be shown later in this article.
As you might imagine, real sales tanked, nearly taking the company down with it. The problem wasn’t limited to counterfeit devices. The actual parts used by the manufacturer were often fake as well. The solution was to create a mechanism for authenticating the supply chain as well as the finished device, which is what they had to do.
OneWheel
OneWheels were unique. They were like skateboards, but instead of the traditional four small wheels, they had one big, fat wheel in the center that let you change directions quickly and even go off-roading. The battery was cleverly hidden inside a solid metal platform that you stood on. The electronics were also stored inside, including advanced circuitry, motor controllers, motion sensors, and wireless communications, so you could adjust the ride settings and monitor battery life with your phone or watch.
The other advantage was that you didn’t have to carry a throttle controller. You just leaned your weight forward and back to make it go in either direction and stood up straight to make it stop. The more forward or backward lean, the faster you went. There were self-balancing algorithms in it, so the platform you stood on would adjust and adapt to give you a smooth ride.
# Side NoteOne late night, after walking a friend (who had a little too much to drink) to his houseboat in Sausalito, I was riding a OneWheel back to my car. A cop car patrolling an empty Bridgeway (the city’s central roadway) passed on the other side of the road. The driver, a young police officer, rolled down the window:
What the heck is that?
OneWheels had a white LED strip in the front and red ones along the back. At night, it looked like the rider was floating on a magic carpet – with appropriate safety lights.
Electric skateboard, I yelled back.
Cool! came the reply.
Want to ride it? I called back.
And that is how I spent an hour at 1 AM, helping two Sausalito Police Officers learn how to ride a OneWheel around a closed gas station lot.
The following year, a story came out of an incident at the Consumer Electronics Show in Las Vegas:
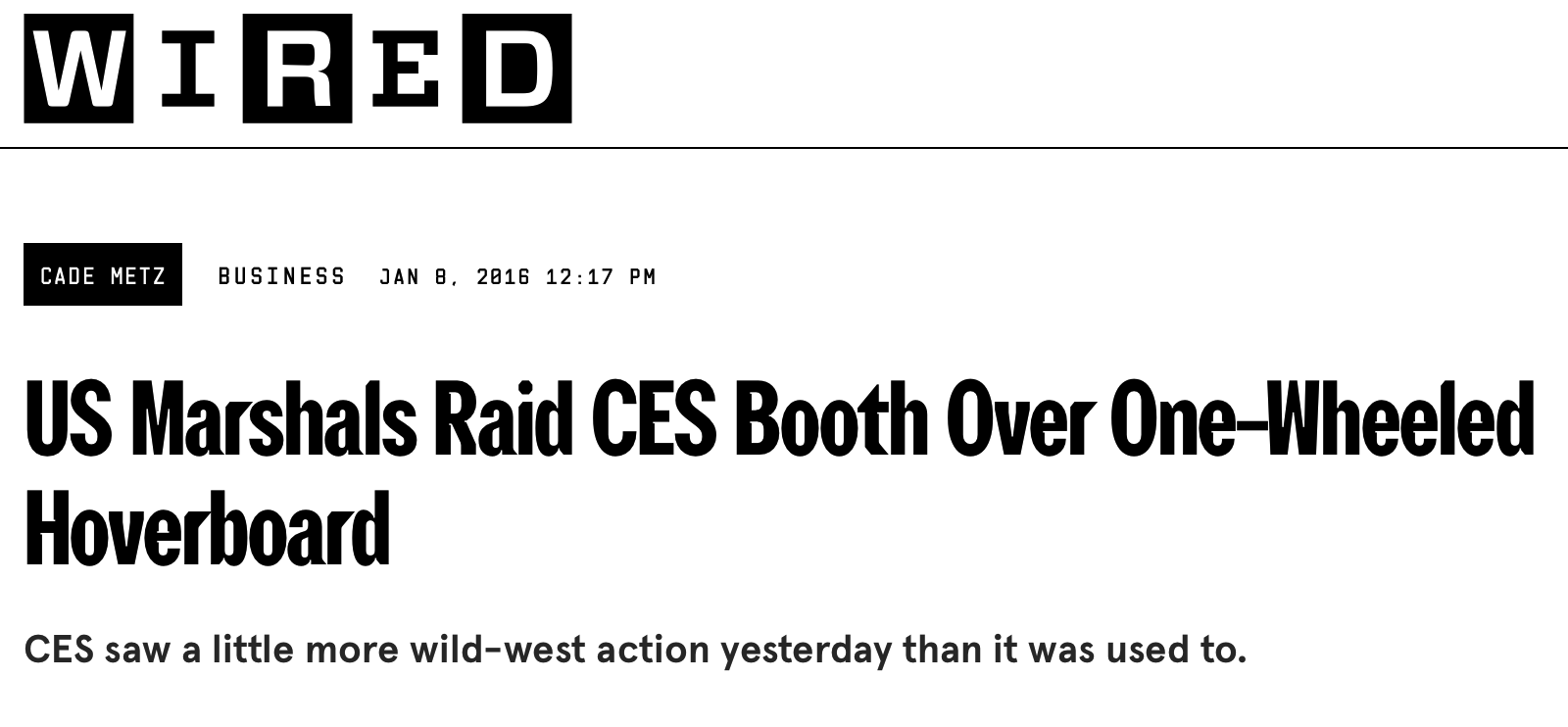
The makers of OneWheel had a copycat problem, but they had nipped it in the bud through hardball, albeit legal means.
What they had in place was a mechanism to identify that the software and the hardware were legitimate and would only work with each other. That, and patents that allowed them to scare away counterfeits before they took hold in the market.
# Full DisclosureIn 2023, FutureMotion had to issue a voluntary recall due to safety issues. Their remedy was to add a ‘haptic buzz’ feature to the boards as a safety alert.
I was long gone by then. But I realized OneWheel could update the firmware and add the feature because they could maintain the attestation chain from manufacturing to individual units, and via secure communication from the back-end servers to phones and on to the boards themselves.
This was not an option for the many counterfeit versions of the original Hoverboard, who were forced out of business.
Matter
Meanwhile, on the connected device side, the Connectivity Standards Alliance (CSA) was trying to solve a similar problem. CSA, as part of their Matter Standard, defined a complex Attestation process for Matter-compliant hardware to prevent hardware counterfeiting (which was a Big Problem).
What Saleae, OneWheel, and CSA faced is the same problem software manufacturers are facing today: how to create and maintain a web of trust. That is what
Friend or Foe?
This problem is endemic to practically every communication channel, from online shopping to car components talking to each other, to counterfeit handbags, scam phone calls, spam emails, pharmaceuticals, and even something as fundamental in modern society as money exchange.
In the software world, one of the methods for stopping malicious code is to
The primary technique we have for this is to create a Root of Trust and allow a trustworthy entity to Vouch for Others along the way. One way for this to work is if, at each stage, there were ways to verify that trust. But not everything is connected at all times. Besides, there is a problem of Man In The Middle Attacks that allows someone to pretend they are someone trustworthy to receive secret information without being entitled to it.
Here’s a small overview of what is involved in the Matter manufacturing process, where the central authority is responsible for handing out verifiable attestation certificates to individual devices:
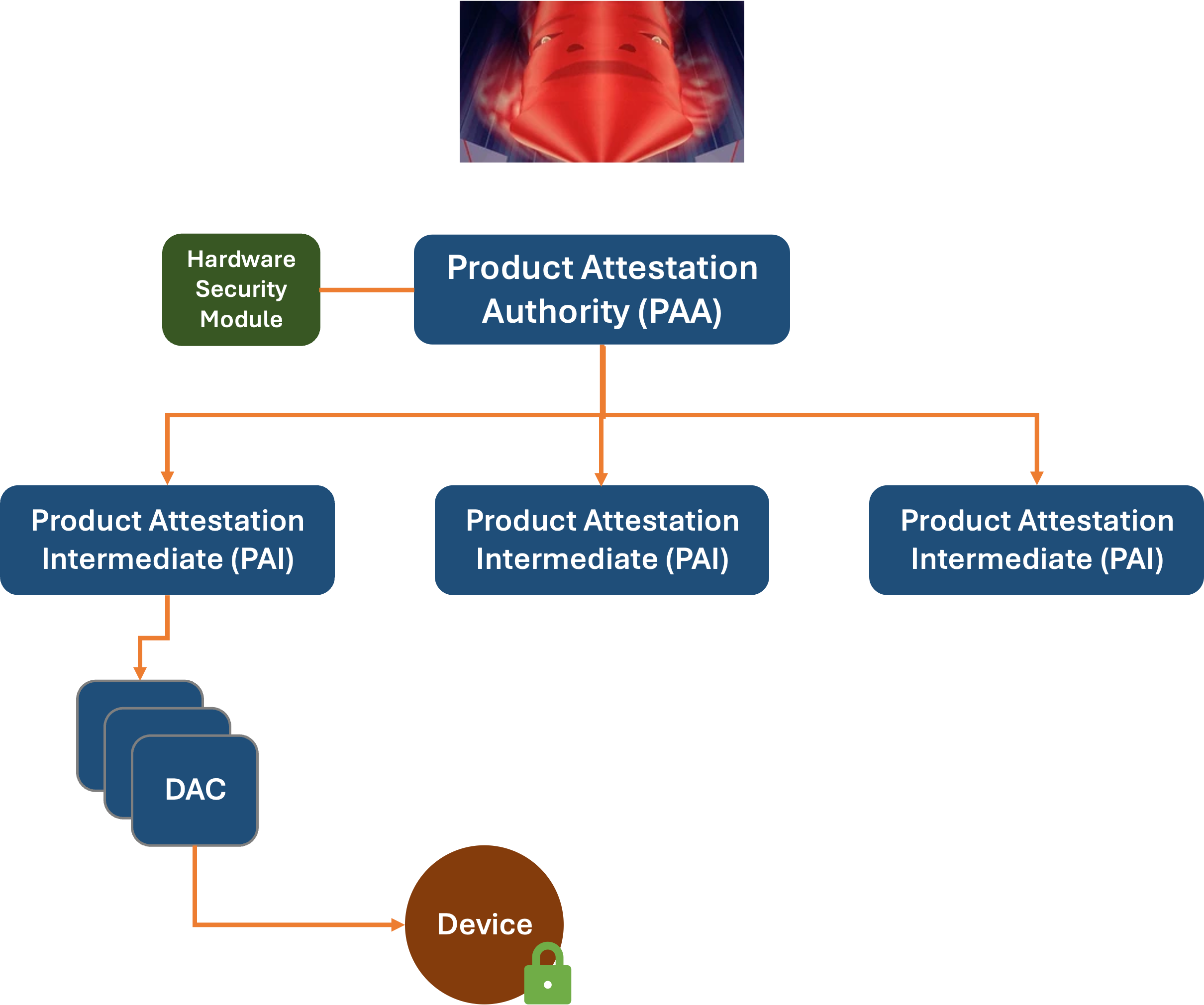
In any scheme, the verification methods would need to support both online and offline modes, and detect tampering. Also important: what to do if something fishy (technical term of art) is detected.
It has taken decades, but a tamperproof piece of hardware containing cryptographically secure keys is the best method we have available to us. Many of these not only store data but also contain secure cryptographic libraries and a co-processor, so they don’t have to rely on potentially tampered external code or malicious code injection. Here are a few examples of these devices:
- Trusted Platform Module (TPM) chip: Used in PCs and servers.
- Apple Secure Enclave: built into the latest versions of iPhone, iPad, Mac, Apple TV, Apple Watch, Apple Vision Pro, and HomePod.
- Google Titan M2: Secure enclave built into Google Pixel phones.
- NXP EdgeLock Secure Enclave: Designed for IoT devices.
- ARM PSA: ARM’s Platform Security Architecture for end-to-end security.
- ARM SSE-710: For embedded systems, including vehicles.
- Microchip ATECC608A: Low-cost security chip.
Before you wrap yourself inside a warm cocoon of security, you should also be aware that just storing things inside a vault is not enough.

You also have to protect the corridors and doors.
And no matter what you do, if someone gets physical access to your device, all bets are off. All it takes is some wire strippers, probes, and a $50 device called the Chip Whisperer Nano.
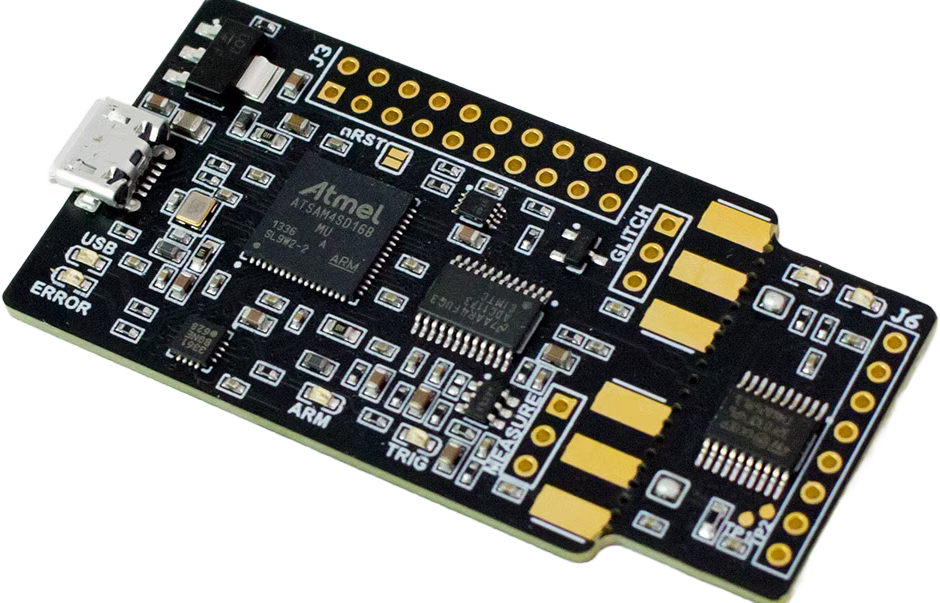
While at it, grab yourself a copy of the Hardware Hacking Handbook to learn different techniques.

There are ways to avoid these security issues. But they require commitment to good design, diligent engineering, and paying attention to all stages of hardware, manufacturing, packaging, distribution, firmware (including OTA updates), mobile, and web, as well as the pathways connecting them all.
You can’t just stick a TPM chip into a hardware design and call it a day. We need a coordinated, integrated end-to-end architecture.

Enter the Governments

In March 2024, the National Coordinator for Critical Infrastructure Security and Resilience (CISA) introduced a proposal for a Secure Software Development Attestation Form and a central repository for depositing software artifacts. US Government agencies have started requiring this from their software vendors.
This problem plagues organizations as buttoned-down and strict as the US DoD.
The European Union has released its own specification called The EU Cyber Resilience Act (CRA). Japan has a slightly different Japan Information Technology Security Evaluation and Certification Scheme (JISEC) model. These are all efforts at verifying the provenance of software applications and libraries.
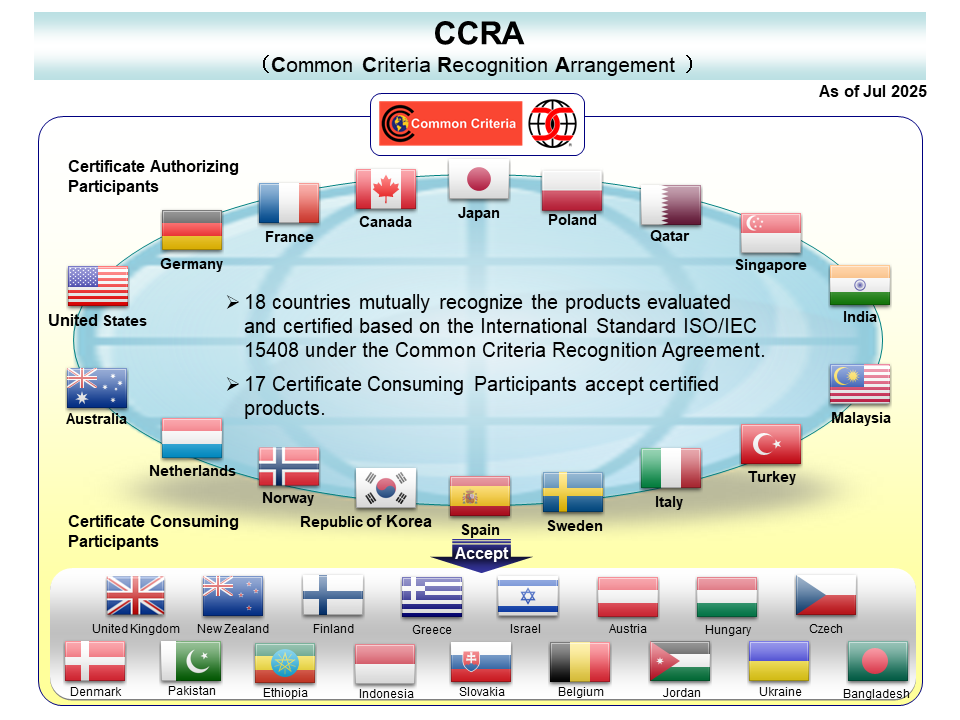
Many other countries (including Japan) also subscribe to the Common Criteria Recognition Arrangement (CCRA) agreement, recognizing a common platform for:
[S]ecurity evaluation criteria for judging whether products and systems related to information technology have been properly designed and whether their designs have been correctly implemented.
China has its own China Information Security (CCIS) Certification service (not to be confused with a similarly named Taiwan credit information agency). However, manufacturer hardware attestation and supply chain tracking are not part of the process.
Private Attestation
Attestation requires building a web of trust on both the provider and consumer sides of services. Absent a central, standard authority, it is up to individual company ecosystems to make sure they implement a way to protect their own customers from harm.
Microsoft, having learned their lessons the hard way, are baking attestation via mandatory code signing into MCP support coming to Windows AI Foundry. This was announced at the Build 2025 conference in May, which Microsoft dubbed The age of AI agents and building the open agentic web.
Apple, as we’ve discussed before, already has device and accessory level verification through its Made for iPhone (MFI) process. This is on top of being one of the founding participants in the Matter specification.
Amazon has its own slightly less rigorous system via the Alexa Mobile Accessory (AMA) specification. It does not require manufacturing certification and attestation. Perhaps it should.
The problem with multiple streams and ecosystems is that none of these devices will interoperate with each other, leaving customers having to navigate a minefield of choices and to restrict themselves to specific models. Manufacturers, too, will have to deal with market fragmentation.
None of this helps make things safer.
Why Does This Matter?

This series is about AI Assistants, deployed in both software and hardware. What does Attestation have to do with any of it?
As AI technology advances, we are seeing it increasingly enter our lives, both explicitly and implicitly. In education, healthcare, business, banking, transportation, space, government, and more. We are trusting our deepest secrets, our bank accounts, and our mental well-being to these systems, whether they deserve to be trusted or not.
If the underlying infrastructure is not hardened adequately against counterfeiting, tampering, Man-In-The-Middle, supply-chain attacks, ransomware, or a range of such problems, we may well end up with headlines that will erode customer trust. And once that trust is gone, it will be hard to get back.
None of us wants to see what may come next.

# Side NoteAs of this writing (June 2025), NONE of the AI extension specifications (MCP or A2A Agent) mentions attestation.
Title Photo by Greg Ortega on Unsplash



